Cyber Security
Cybersecurity
Be Job-Ready! Upskill yourself in relevant skills and knowledge
We offer the best-in-class brands in the fields of Cybersecurity. Our Instructors, who are practitioners in their respective fields, come with years of hands-on industry experience and have been certified by the best-in-class brands after going through a rigorous accreditation process. Majority of our courses are aligned to certification exam syllabus and will help trainees to prepare for globally recognised IT certifications.
We have the capability to contextualize training and content to the needs of companies and learners. We understand that each company has its own unique needs and requirements when it comes to training, and we have a team of subject matter experts who can tailor our courses specifically to the needs of your business. This ensures that each employee receives the most relevant training possible, which will help them function more efficiently and effectively to maximise their contribution to your business.
As a one-stop ecosystem of training and assessment solutions, NTUC LearningHub is also the largest computer-based Testing center in Singapore, offering and facilitating in-demand certification exams delivered via platforms such as Pearson VUE, PSI, Kryterion, Certiport, etc for your employees.
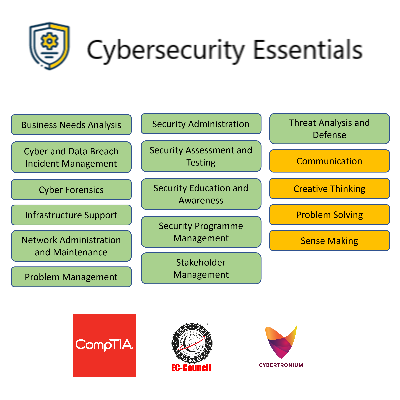
Entry Level: Associate Security Analyst
Singapore’s Smart Nation initiative means that there is an increasing need for cybersecurity analysts. As the country moves towards a unified e-payment system and programs like digital tech for low-income households, internet of things for healthcare, and logistics for shopping malls.
To start of a career in Cybersecurity, the role of an Associate Security Analyst is critical, and he/she supports security systems, operations administration, monitoring and maintenance of cyber security systems and applications. He/she monitors security alerts and events, collects and document information based on established practices and supports the preparation and publishing of security advisories.
He/she assists with the analysis of security-related information and events, escalation of incidents for validation and remediation. He/she must be familiar with cyber security standards, protocols and frameworks.

Entry Level Cybersecurity Competency Requirements:
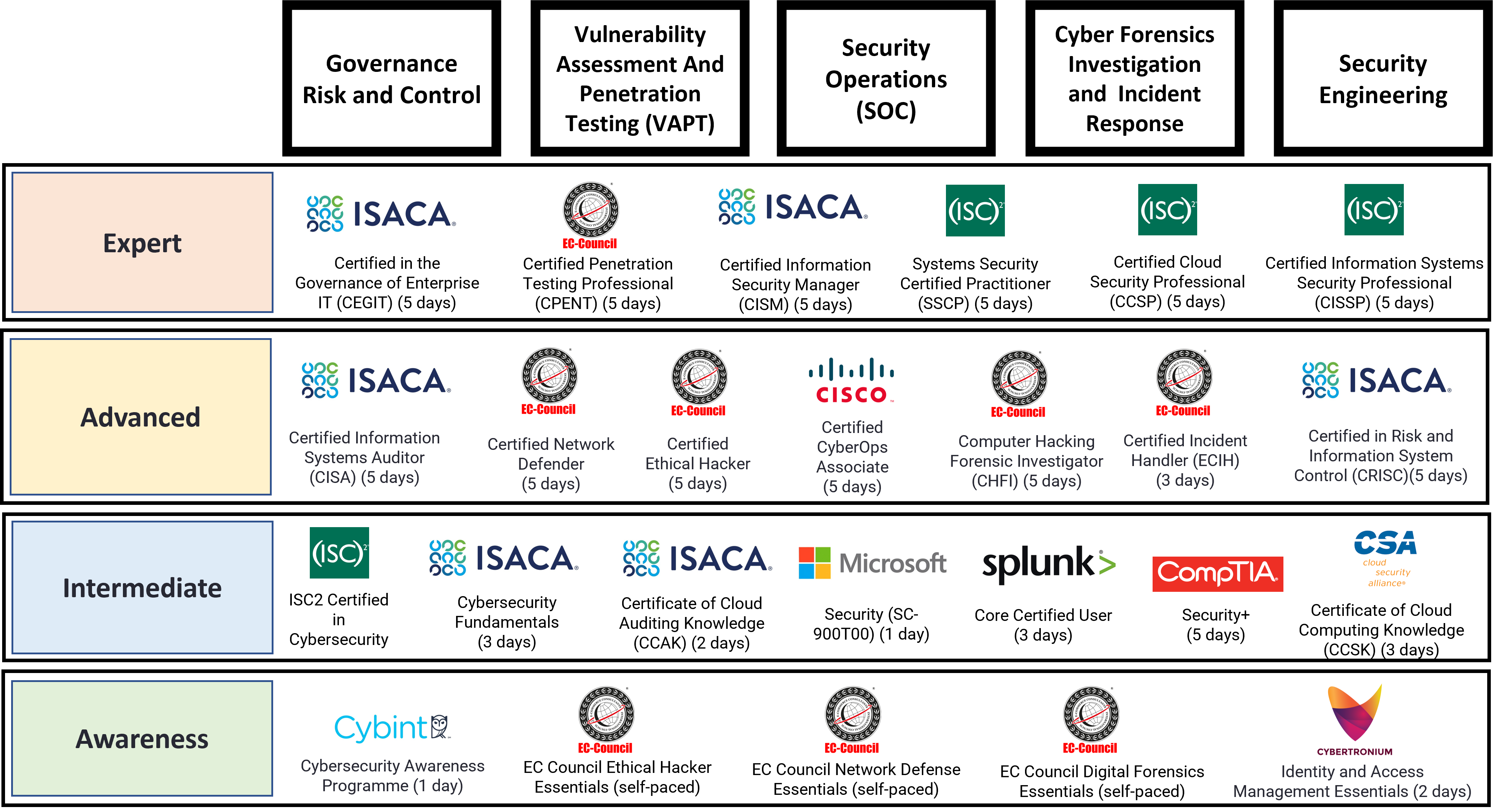
Specialisation: 6 Cybersecurity Roles
Cybersecurity Job Roles x Certification Courses