IT17B11: EC-COUNCIL CERTIFIED ETHICAL HACKER (CEH) (SF) (SYNCHRONOUS E-LEARNING)

EC-COUNCIL CERTIFIED ETHICAL HACKER (CEH) (SF) (SYNCHRONOUS E-LEARNING)
Course Duration
Mode of Assessment
- Students will be required to complete a written assessment during class. There are 2 assessment modes in this module: Short Answer Question and Case Study
- External Certification Exam
- After completing the course, students can proceed to undertake the EC Council Certified Ethical Hacker exam. NTUC LHUB will issue an exam voucher and candidates may proceed to book the official “EC Council Certified Ethical Hacker” exam (valid for 1 year after you have submitted course evaluation via Aspen Portal)
Who Should Attend
This course is designed for anyone seeking an active role in the field of information security.
The job roles best suited to the material in this course are:
- Information Security Analyst / Administrator
- Information Assurance (IA) Security Officer
- Information Security Manager / Specialist
- Information Systems Security Engineer / Manager
- Information Security Professionals / Officers
- Information Security / IT Auditors
- Risk / Threat/Vulnerability Analyst
- System Administrators
- Network Administrators and Engineers
What's In It for Me
- CEHv12 e-book for 24 months access (After you have registered an Aspen account and entered the subscription access code issued to you via email)
- CEH exam voucher valid for 12 months
- CEHv12 iLab for 6 months access
- Next version e-book
- CEH Re-exam voucher x Unlimited (only for CEH ANSI exam)
- CodeRed Ethical Hacking Videos x 10, 1 year access
- CEH Engage on CyberQ, 1 year access
- Global CEH Challenge on CyberQ, 1 year access
- CEH Exam Prep Kit (1 x Mock Test), 1 year access
- CEH Practical Exam Voucher, valid for 1 year
- Certificate of Attendance (after you have submitted course evaluation via Aspen Portal)
- Certificate of Award (after you have passed the exam which will be proctored at NTUC LearningHub)
Course Overview

The Certified Ethical Hacker has been battle-hardened over the last 20 years, creating
hundreds of thousands of Certified Ethical Hackers employed by top companies, militaries,
and governments worldwide.
In its 12th version, the Certified Ethical Hacker provides comprehensive training, handson
learning labs, practice cyber ranges for engagement, certification assessments, cyber
competitions, and opportunities for continuous learning into one comprehensive program
curated through our new learning framework: 1. Learn 2. Certify 3. Engage 4. Compete.
The C|EH v12 also equips aspiring cybersecurity professionals with the tactics, techniques,
and procedures (TTPs) to build ethical hackers who can uncover weaknesses in nearly any
type of target system before cybercriminals do.

- You will be able to describe the basics of network and Internet accessible application technologies, common discovery, and analysis techniques as well as more advanced security concepts such as malware and cryptography.
- Learn about the latest commercial-grade hacking tools, techniques, and methodologies used by hackers and information security professionals to lawfully hack an organisation.
Course Schedule
Next available schedule
Course Objectives

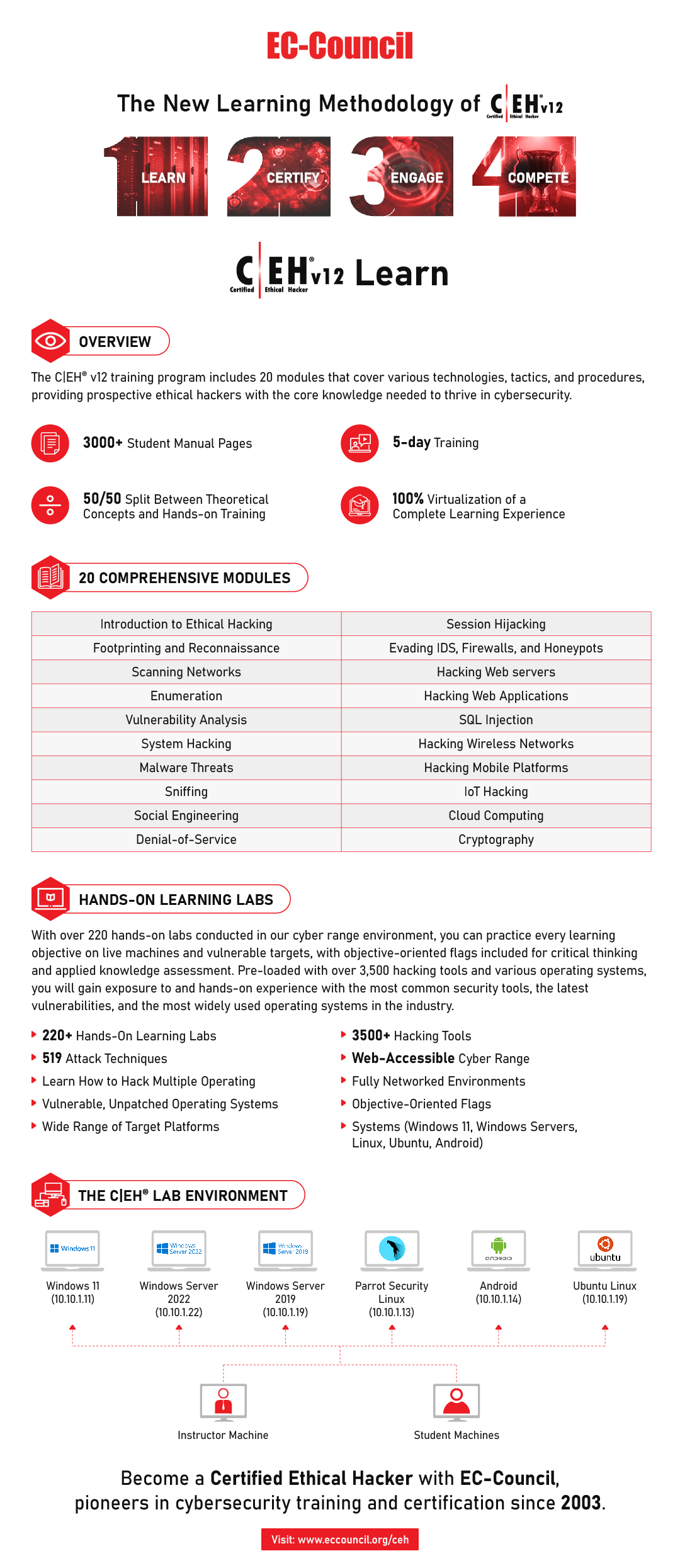
The C|EH® v12 training program includes 20 modules covering various technologies, tactics, and procedures, providing prospective ethical hackers with the core knowledge needed to thrive in cybersecurity. Delivered through a carefully curated training plan that typically spans five days, the 12th version of the C|EH® continues to evolve to keep up with the latest OS, exploits, tools, and techniques. The concepts covered in the training program are split 50/50 between knowledge-based training and hands-on application through our cyber range.Every tactic discussed in training is backed by step-by-step labs conducted in a virtualized environment with live targets, live tools, and vulnerable systems. Through our lab technology, every participant will have comprehensive hands-on practice to learn and apply their knowledge.”
With over 220 hands-on labs conducted in our cyber range environment, you will have the opportunity to practice every learning objective on live machines and vulnerable targets in the course. Pre-loaded with over 3,500 hacking tools and various operating systems, you will
gain unprecedented exposure and hands-on experience with the most common security tools, latest vulnerabilities, and widely used operating systems in the industry. Our range is web accessible, making it easier for you to learn and practice from anywhere.
What’s Covered:
- 100% virtualization for a complete learning experience
- After login, you will have full access to preconfigured targets, networks, and the attack tools necessary to exploit them:
• Pre-configured vulnerable websites
• Vulnerable, unpatched operating systems
• Fully networked environments
• 3,500+ hacking tools
• And much more!
- Wide range of target platforms to hone your skills
- Objective-oriented flags for critical thinking and applied knowledge assessment
- Cloud-based cyber range
- 519 attack techniques
Upon completing the course, students will be able to:
- Carry out threat modelling and secured source code review
- Conduct authorised penetration testing of systems consisting of a range of penetration testing methodologies, tools and techniques
- Use a suite of network monitoring and vulnerability scanning tools to assess the threats and vulnerabilities in a system
- Identify vulnerability exploitations and potential attack vectors into a system
- Analyse vulnerability scan results to size and assess security loopholes and threats
- Evaluate if current systems can overcome emerging threats and hacking techniques
- Assess current security practices and controls against expected performance parameters or guidelines
- Develop a vulnerability assessment and penetration testing report, highlighting key threats and areas for improving system security
- Understand process and techniques for secured source code review
- Identify threat modelling techniques
- Discover penetration testing techniques and methodologies
- Identify penetration testing tools and their usage
- Understand network monitoring tools and their usage
- Understand vulnerability assessment tests and interpretation of results
- Identify range and types of security loopholes and threats
(* Please note registration for class needs to be 1 week prior to class start date)
Pre-requisites
Knowledge, Skills & Experience
You should have some foundational knowledge and skills in network security and IT.
While there are no formal prerequisites for CEH certification, you should demonstrate a good understanding of the exam topics and some familiarity and or experience in information security.
It is recommended that you have prior formal trainings in the following:
-
CompTIA A+
-
CompTIA Network +
-
CompTIA Security+
-
EC-Council Certified Network Defender (CND) (SF)
Bonus*
For Learner's who do not have any prior network security knowledge, after signing up for this course we will be giving you a free Network Defense Essentials (NDE) and Ethical Hacking Essentials (EHE) E-Book and Video uploaded on CANVAS to prepare you. Please note that these additional online resources are found on your CANVAS and not separately delivered to you.
Click on the photo below to find out more:
Recommended for Career Path Advancement
-
EC Council Computer Hacking Forensic Investigator (CHFI) (For Incident Response and Forensics)
-
EC Council Certified Incident Handler (ECIH) (For Incident Response and Forensics)
-
EC Council Certified SOC Analyst (CSA) (For SOC Operations)
-
Cisco CCNA Cyber Security Operations (For SOC Operations)
-
ISC2 Certified Information Systems Security Professional (CISSP) (For Security Engineer)
-
Certificate of Cloud Auditing Knowledge (CCAK) (For Cloud Security)
-
ISC2 Certified Cloud Security Professional (CCSP) (For Cloud Security)
Hardware & Software
This course will be conducted as a Virtual Live Class (VLC) via Zoom platform. Participants must own a zoom account and have a laptop or a desktop with “Zoom Client for Meetings” installed. This can be downloaded from https://zoom.us/download.
|
System Requirement |
|
Must Have: Please ensure that your computer or laptop meets the following requirements.
Good to Have:
Not Recommended: |
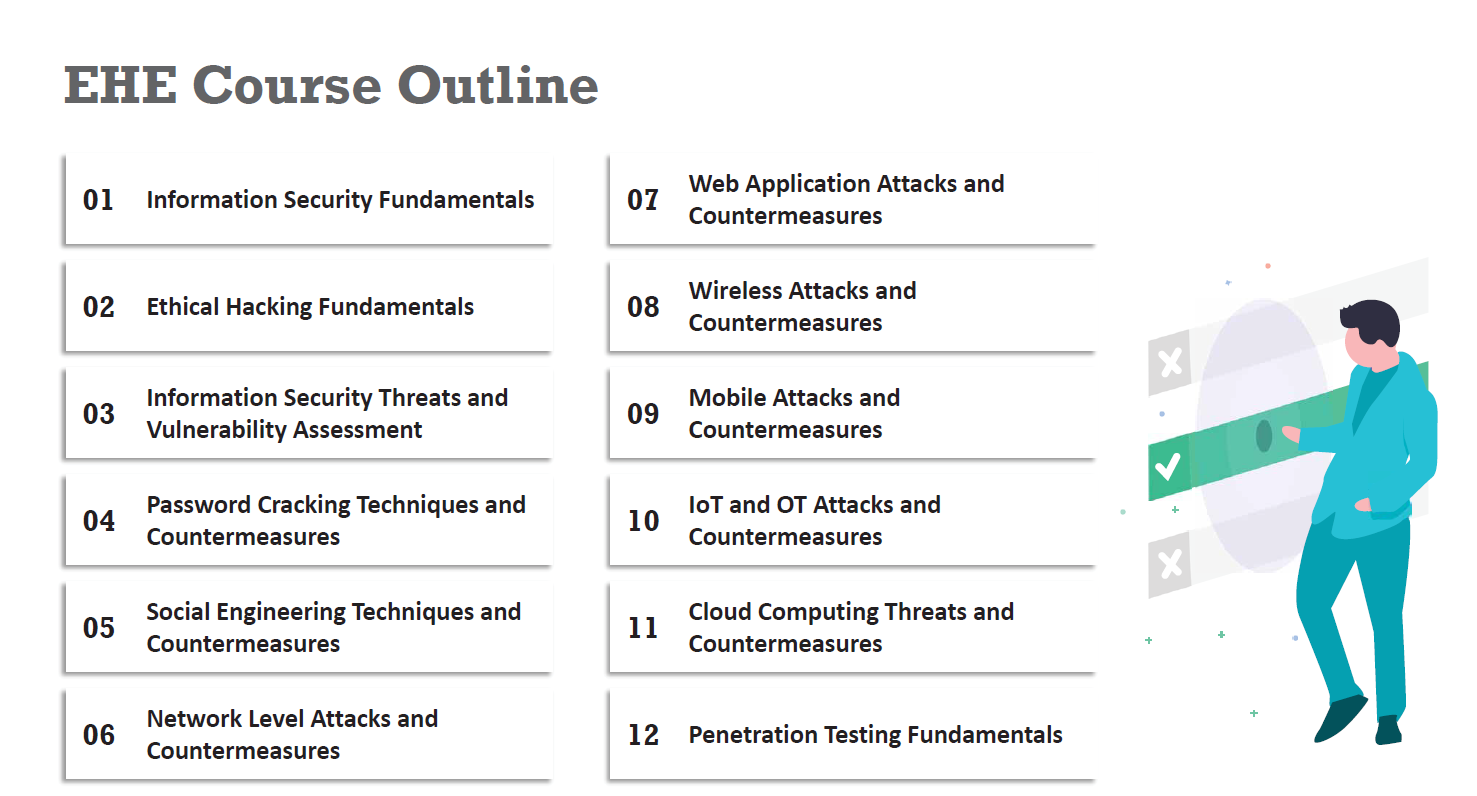
Course Outline

Course Outline
1. New Learning Methodology: Learn – Certify – Engage – Compete
2. Compete: new challenges every month to test your job-ready skills!
3. 100% Compliance to NICE 2.0 Framework
4. Based on a comprehensive industry-wide job-task analysis
5. Hands-on learning labs
6. Practice Range
7. Global C|EH community competitions
8. Cheat Sheet
9. Coverage of the latest malware
10. Lab-intensive program (Every learning objective is demonstrated using labs)
11. Hands-on program (More than 50% of training time is dedicated to labs)
12. Lab environment simulates a real-time environment(Lab setup simulates real-life networks and platforms)
13. Covers the latest hacking tools (Based on Windows, macOS, and Linux)
14. Latest OS covered and a patched testing environment
15. All the tool screenshots are replaced with the latest version
16. All the tool listing slides are updated with the latest tools
17. All the countermeasure slides are updated
Technology Updates:
1. MITRE ATTACK Framework
2. Diamond Model of Intrusion Analysis
3. Techniques for Establishing Persistence
4. Evading NAC and Endpoint Security
5. Fog Computing
6. Edge Computing
7. Grid Computing


Certificate Obtained and Conferred by
- Certificate of Completion from NTUC LearningHub
Upon meeting at least 75% attendance and passing the assessment(s), participants will receive a Certificate of Completion from NTUC LearningHub.
- Statement of Attainment (SOA) from SkillsFuture Singapore
After passing the assessment(s), participants will receive a SOA from SkillsFuture Singapore, certifying that they have achieved the following Competency Standard(s):
- ICT-DIT-3012-1.1 Security Assessment and Testing
- External Certification
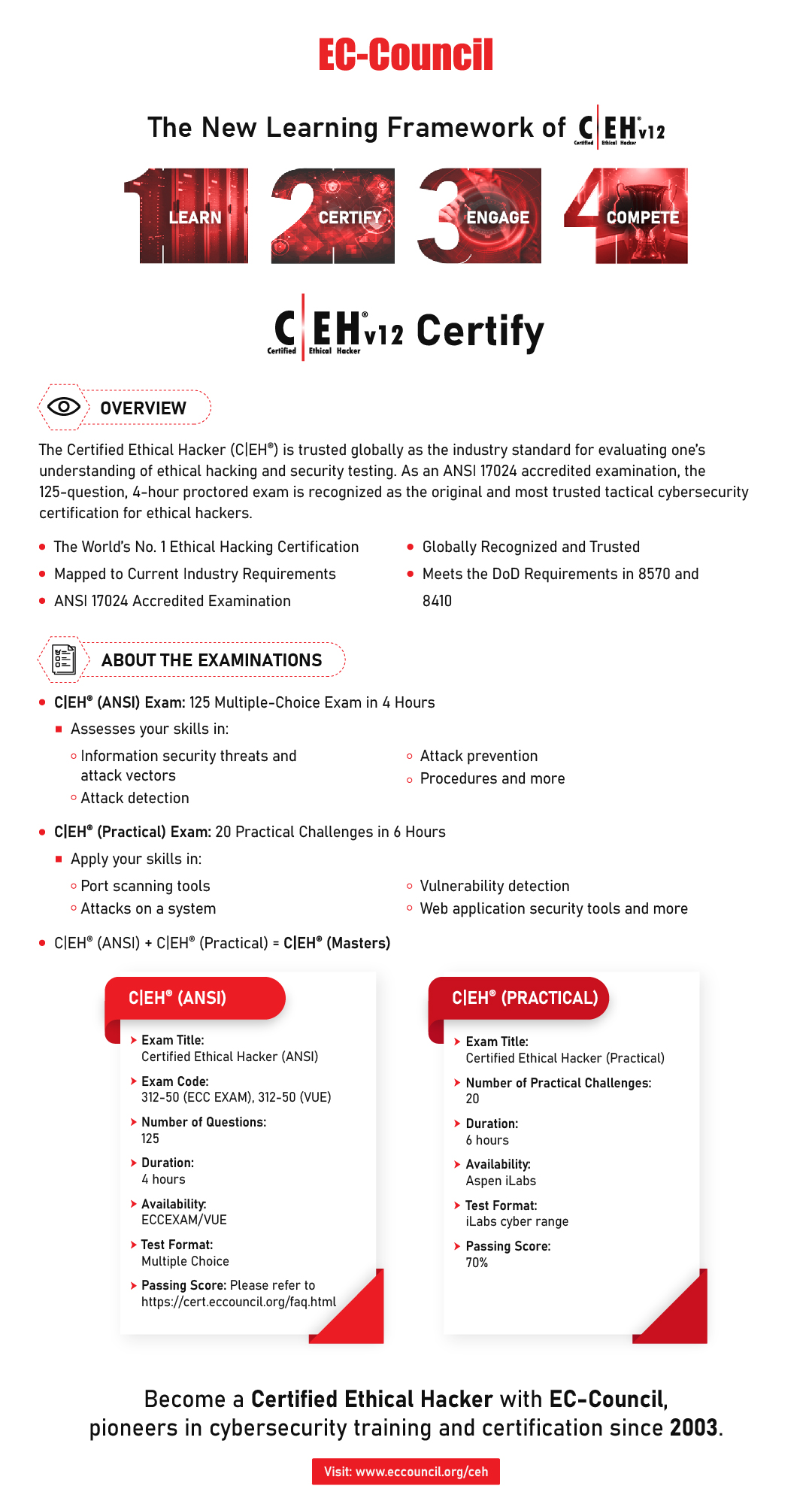
The participant will be able to attempt the Certified Ethical Hacker (ANSI) Certification Exam after attending this course. Upon passing the exam, you will receive the Certified Ethical Hacker (ANSI) Certificate. This certification credential is trusted globally as the industry standard for evaluating one’s understanding of ethical hacking and security testing.
- C|EH® (ANSI) Exam Fee
The course fee includes the C|EH® (ANSI) certification exam fee for trainees who attend and complete the EC-Council Certified Ethical Hacker (CEH) course with NTUC LearningHub.
For subsequent exam attempts, the C|EH® (ANSI) certification exam voucher can be purchased at the full fee from our Exam e-shop or contact [email protected]
Exam Code: 312-50 (ECC EXAM), 312-50 (VUE)
Exam duration: 4 hours
Exam format: 125 multiple choice questions
Passing score: https://cert.eccouncil.org/faq.html
You will be awarded with the following digital badge(s) upon passing the official C|EH® (ANSI) exam:
Additional Details
Medium of Instruction: English
Trainer to trainee ratio: 1:20
Mode of Delivery: Virtual Live Class (VLC) via Zoom or Physical class (F2F)
Courseware (valid till June 2024):
- CEHv12 e-book for 24 months access (After you have registered an Aspen account and entered the subscription access code issued to you via email)
- CEH exam voucher valid for 12 months
- CEHv12 iLab for 6 months access
- Next version e-book
- CEH Re-exam voucher x Unlimited (only for CEH ANSI exam)
- CodeRed Ethical Hacking Videos x 10, 1 year access
- CEH Engage on CyberQ, 1 year access
- Global CEH Challenge on CyberQ, 1 year access
- CEH Exam Prep Kit (1 x Mock Test), 1 year access
- CEH Practical Exam Voucher, valid for 1 year
Price
|
Course Fee and Government Subsidies |
||||||
|
|
Individual Sponsored |
Company Sponsored |
||||
|
Non-SME |
SME |
|||||
|
Before GST |
After GST |
Before GST |
After GST |
Before GST |
After GST |
|
|
Full Course Fee (For Foreigners and those not eligible for subsidies) |
$2,700.00 |
$2,943.00 |
$2,700.00 |
$2,943.00 |
$2,700.00 |
$2,943.00 |
|
For Singapore Citizens aged 39 and below and For all Singapore Permanent Residents (The minimum age for individual sponsored trainees is 21 years) |
$1,350.00 |
$1,593.00 |
$1,350.00 |
$1,593.00 |
$810.00 |
$1,053.00 |
|
For Singapore Citizens aged 40 years and above |
$810.00 |
$1,053.00 |
$810.00 |
$1,053.00 |
$810.00 |
$1,053.00 |
Funding Eligibility Criteria
|
Individual Sponsored Trainee |
Company Sponsored Trainee |
|
|
Remarks
|
Company Sponsored Trainee |
|
|
SkillsFuture Credit:
PSEA:
|
Absentee Payroll (AP) Funding:
|
Terms & Conditions apply. NTUC LearningHub reserves the right to make changes or improvements to any of the products described in this document without prior notice.
Prices are subject to other LHUB miscellaneous fees.
| Batch ID | Course Period | Course Title | Funding Available |
Duration (Hours) |
Session (Hours) |
Venue | Available Seats |
Online Payment |
|---|
What Others Also Enrolled In

EC-COUNCIL CERTIFIED NETWORK DEFENDER (CND) (SF) (SYNCHRONOUS E-LEARNING)
View detail
EC-COUNCIL CERTIFIED PENETRATION TESTING PROFESSIONAL (CPENT) (SF)
View detail
EC-COUNCIL CERTIFIED ETHICAL HACKER (CEH) (SF) (SYNCHRONOUS E-LEARNING)
View detail
EC-COUNCIL CERTIFIED SOC ANALYST (CSA) (SYNCHRONOUS E-LEARNING)
View detail